Microsoft’s January 2025 Patch Tuesday Addresses 157 CVEs (CVE-2025-21333, CVE-2025-21334, CVE-2025-21335)
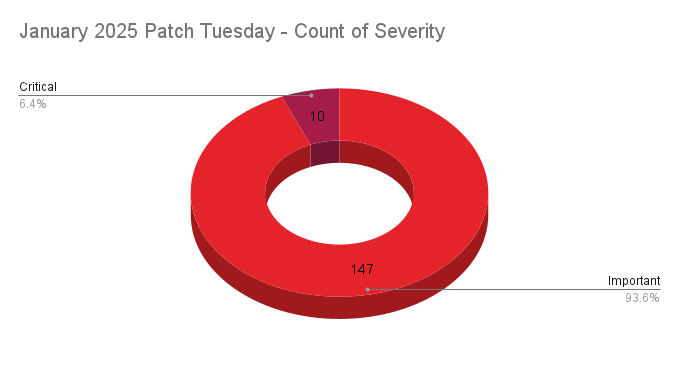
- 10Critical
- 147Important
- 0Moderate
- 0Low
Microsoft addresses 157 CVEs in the first Patch Tuesday release of 2025 and the largest Patch Tuesday update ever with three CVEs exploited in the wild, and five CVEs publicly disclosed prior to patches being made available.
Microsoft patched 157 CVEs in its January 2025 Patch Tuesday release, with 10 rated critical and 147 rated as important. Our counts omitted two vulnerabilities, one reported by GitHub and another reported by CERT/CC. To date, the January 2025 Patch Tuesday release is the largest ever from Microsoft.
This month’s update includes patches for:
- .NET
- .NET and Visual Studio
- .NET,.NET Framework, Visual Studio
- Active Directory Domain Services
- Active Directory Federation Services
- Azure Marketplace SaaS Resources
- BranchCache
- IP Helper
- Internet Explorer
- Line Printer Daemon Service (LPD)
- Microsoft AutoUpdate (MAU)
- Microsoft Azure Gateway Manager
- Microsoft Brokering File System
- Microsoft Digest Authentication
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office OneNote
- Microsoft Office Outlook
- Microsoft Office Outlook for Mac
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft Purview
- Microsoft Windows Search Component
- Power Automate
- Reliable Multicast Transport Driver (RMCAST)
- Visual Studio
- Windows BitLocker
- Windows Boot Loader
- Windows Boot Manager
- Windows COM
- Windows Client-Side Caching (CSC) Service
- Windows Cloud Files Mini Filter Driver
- Windows Connected Devices Platform Service
- Windows Cryptographic Services
- Windows DWM Core Library
- Windows Digital Media
- Windows Direct Show
- Windows Event Tracing
- Windows Geolocation Service
- Windows Hello
- Windows Hyper-V NT Kernel Integration VSP
- Windows Installer
- Windows Kerberos
- Windows Kernel Memory
- Windows MapUrlToZone
- Windows Mark of the Web (MOTW)
- Windows Message Queuing
- Windows NTLM
- Windows OLE
- Windows PrintWorkflowUserSvc
- Windows Recovery Environment Agent
- Windows Remote Desktop Services
- Windows SPNEGO Extended Negotiation
- Windows Security Account Manager
- Windows Smart Card
- Windows SmartScreen
- Windows Telephony Service
- Windows Themes
- Windows UPnP Device Host
- Windows Virtual Trusted Platform Module
- Windows Virtualization-Based Security (VBS) Enclave
- Windows WLAN Auto Config Service
- Windows Web Threat Defense User Service
- Windows Win32K - GRFX
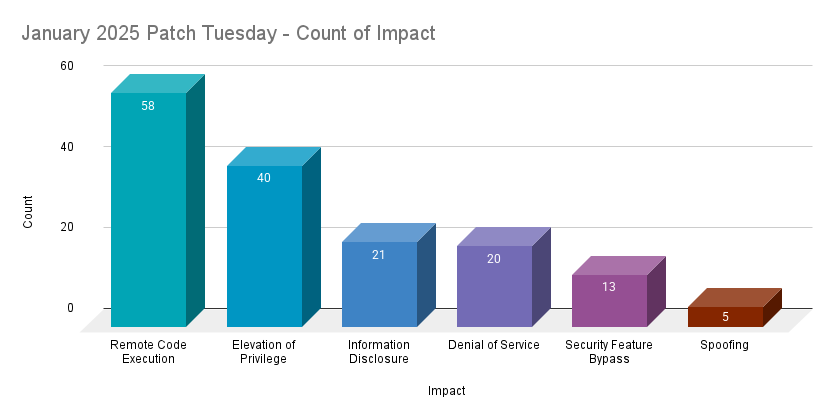
Remote code execution (RCE) vulnerabilities accounted for 36.9% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 25.5%.
CVE-2025-21333, CVE-2025-21334, CVE-2025-21335 | Windows Hyper-V NT Kernel Integration VSP Elevation of Privilege Vulnerabilities
CVE-2025-21333, CVE-2025-21334 and CVE-2025-21335 are EoP vulnerabilities in the Windows Hyper-V NT Kernel Integration Virtualization Service Provider (VSP). All three vulnerabilities were assigned a CVSSv3 score of 7.8 and rated important. An authenticated, local attacker could exploit this vulnerability to elevate privileges to SYSTEM. Two of the three vulnerabilities were unattributed, with CVE-2025-21333 being attributed to an Anonymous researcher.
According to Microsoft all three vulnerabilities were exploited in the wild as zero-days. No specific details about the in-the-wild exploitation were public at the time this blog post was released.
CVE-2025-21186, CVE-2025-21366, CVE-2025-21395 | Microsoft Access Remote Code Execution Vulnerability
CVE-2025-21186, CVE-2025-21366 and CVE-2025-21395 are RCE vulnerabilities in Microsoft Access, a database management system. All three vulnerabilities were assigned a CVSSv3 score of 7.8 and rated important. A remote, unauthenticated attacker could exploit this vulnerability by convincing a target through social engineering to download and open a malicious file. Successful exploitation would grant an attacker arbitrary code execution privileges on the vulnerable system. This update “blocks potentially malicious extensions from being sent in an email.”
According to Microsoft, these three vulnerabilities were publicly disclosed prior to a patch being available (zero-days). They are attributed to Unpatched.ai, which uses artificial intelligence (AI) to “help find and analyze” vulnerabilities.
CVE-2025-21308 | Windows Themes Spoofing Vulnerability
CVE-2025-21308 is a spoofing vulnerability affecting Windows Themes. This vulnerability received a CVSSv3 score of 6.5 and was publicly disclosed prior to a patch being made available. According to Microsoft, successful exploitation requires an attacker to convince a user to load a malicious file, then convince the user to “manipulate the specially crafted file.” Microsoft has provided a list of mitigations including disabling New Technology LAN Manager (NTLM) or using group policy to block NTLM hashes. For more information on the mitigation guidance, please refer to the Microsoft advisory.
CVE-2025-21275 | Windows App Package Installer Elevation of Privilege Vulnerability
CVE-2025-21275 is an EoP vulnerability in the Microsoft Windows App Package Installer. It was assigned a CVSSv3 score of 7.8 and is rated important. A local, authenticated attacker could exploit this vulnerability to obtain SYSTEM privileges. These types of flaws are often associated with post-compromise activity, after an attacker has breached a system through other means.
According to Microsoft, this vulnerability was publicly disclosed prior to a patch being available. It is attributed to an Anonymous researcher.
CVE-2025-21297, CVE-2025-21309 | Windows Remote Desktop Services Remote Code Execution Vulnerability
CVE-2025-21297 and CVE-2025-21309 are critical RCE vulnerabilities affecting Windows Remote Desktop Services. Both of these vulnerabilities were assigned CVSSv3 scores of 8.1, however CVE-2025-21309 was assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index, while CVE-2025-21297 was assessed as “Exploitation Less Likely.”
According to Microsoft, successful exploitation of these flaws requires an attacker to connect to a system with the Remote Desktop Gateway role and trigger a race-condition that creates a use-after-free scenario which can be leveraged to execute arbitrary code.
CVE-2025-21298 | Windows OLE Remote Code Execution Vulnerability
CVE-2025-21298 is a RCE vulnerability in Microsoft Windows Object Linking and Embedding (OLE). It was assigned a CVSSv3 score of 9.8 and is rated critical. It has been assessed as “Exploitation More Likely.” An attacker could exploit this vulnerability by sending a specially crafted email to a target. Successful exploitation would lead to remote code execution on the target system if the target opens this email using a vulnerable version of Microsoft Outlook or if their software is able to preview the email through a preview pane.
Microsoft’s advisory for this vulnerability recommends configuring Microsoft Outlook to read email messages “in plain text format” instead of a rich format that will display other types of content, such as photos, animations or specialized fonts. To configure Outlook in this way, please refer to the following article, Read email messages in plain text.
Tenable Solutions
A list of all the plugins released for Microsoft’s January 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's January 2025 Security Updates
- Tenable plugins for Microsoft January 2025 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

The post Microsoft’s January 2025 Patch Tuesday Addresses 157 CVEs (CVE-2025-21333, CVE-2025-21334, CVE-2025-21335) appeared first on Security Boulevard.